
Photo by Glen Alejandro on Unsplash
U.S. Government Funding For CVE Cybersecurity Program Set to Expire
- Written by Andrea Miliani Former Tech News Expert
- Fact-Checked by Sarah Frazier Former Content Manager
The Common Vulnerabilities and Exposures (CVE) program faces an uncertain future as the U.S. government has not renewed its contract to support the initiative through the nonprofit organization MITRE, and it expires today, April 16. Cybersecurity experts are now warning of potential global security consequences.
In a rush? Here are the quick facts:
- The U.S. government will not renew the contract to provide financial support to the CVE program, and it expires today.
- The non-profit organization has sent a letter to CVE board members and assures the government is searching for alternatives.
- Cybersecurity experts are concerned and warn about global disruption and confusion.
The CVE program, launched in 1999, has been designed to develop an ID system and help engineers and organizations identify, apply patches, and mitigate vulnerabilities worldwide. Considering a code that begins with the letters “CVE” followed by the year and a unique number—such as CVE-2024-50050 found in Meta’s AI Framework or the Chrome zero-day vulnerability CVE-2025-2783 spotted a few weeks ago—the program organizes and keeps control of global vunerabilities.
The MITRE Corporation has been maintaining and operating the CVE system since its founding and has been consistently receiving financial support from the Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA) for the past 25 years.
An internal letter sent from Yosry Barsoum, VP and Director of the Center for Securing the Homeland (CHS) at MITRE, to board members of the CVE has been leaked and shared publicly on Bluesky .
“We want to make you aware of an important potential issue with MITRE’s enduring support to CVE,” states the document. “On Wednesday, April 16, 2025, the current contracting pathway for MITRE to develop, operate, and modernize CVE and several other related programs, such as CWE, will expire.”
The Verge has confirmed the information disclosed on the social media platform and reached out to Barsoum who assured that the government is making efforts to continuing to support MITRE, and that, in the meantime, the Common Weakness Enumeration (CWE) program—which focuses on software and hardware vulnerabilities—will also be affected.
Cybersecurity researcher Lukasz Olejnik shared his concerns on X. “The Trump administration will effectively (at least temporarily) cripple the global cybersecurity system,” he wrote in a post. “The consequence will be a breakdown in coordination between vendors, analysts, and defense systems — no one will be certain they are referring to the same vulnerability. Total chaos, and a sudden weakening of cybersecurity across the board.”
By cutting what amounts to penny costs, the Trump administration will effectively (at least temporarily) cripple the global cybersecurity system — CVE. What is CVE? It is a global system for identifying and tracking vulnerabilities that has served as a common language for… pic.twitter.com/WBCdLz0DdT — Lukasz Olejnik (@lukOlejnik) April 15, 2025
Other experts and organizations, including MITRE, expect to find other funding sources and alternatives for the CVE program to continue its service and operations regularly.
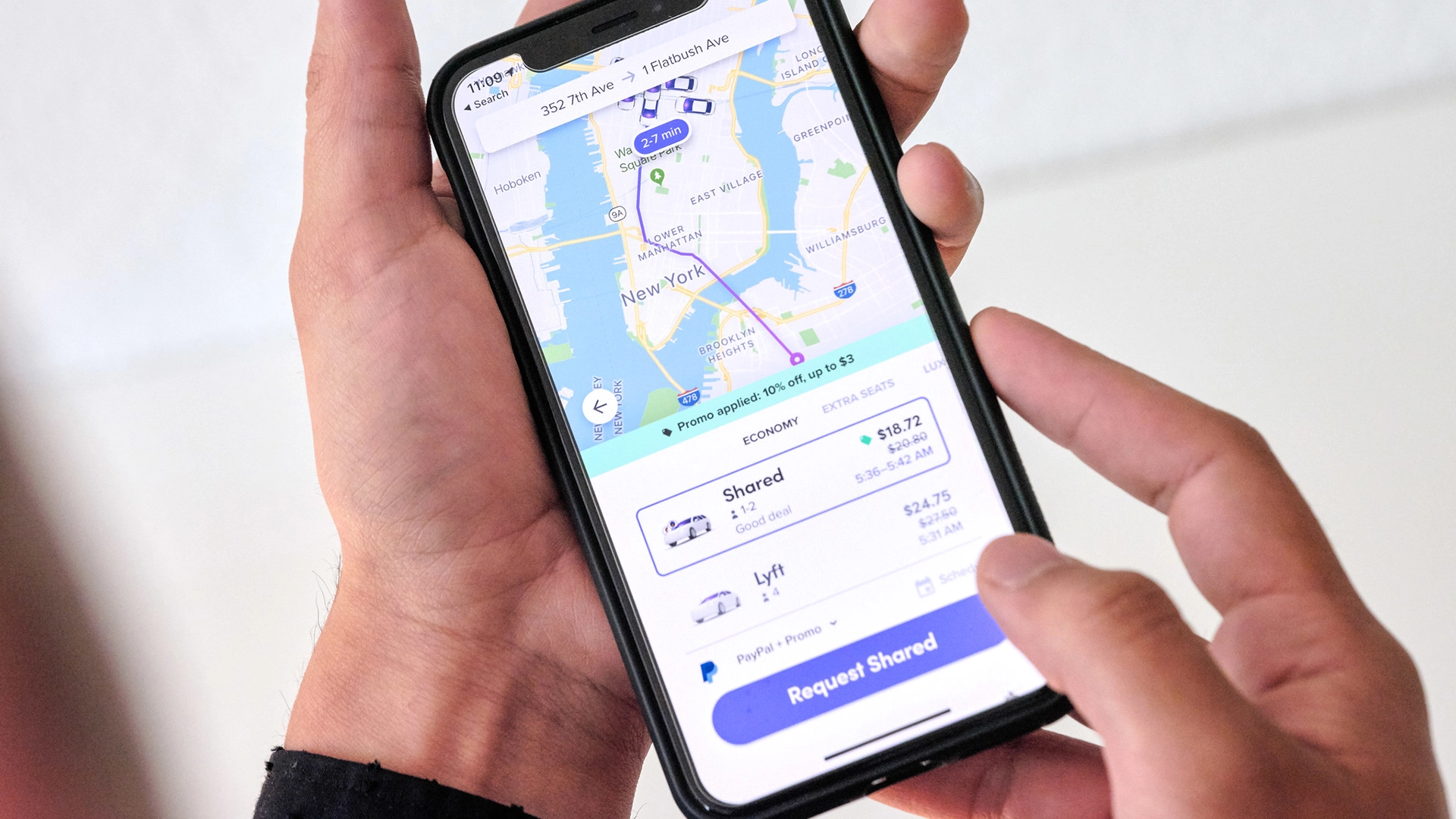
Image by Daniel Foster, from Flickr
Lyft Passenger Gets Mysterious Text Containing Recorded In-Ride Conversation
- Written by Kiara Fabbri Former Tech News Writer
- Fact-Checked by Sarah Frazier Former Content Manager
A Toronto woman received a transcript of her private Lyft conversation, raising serious questions about rider privacy and informed consent under Canadian law.
In a rush? Here are the quick facts:
- Woman received transcript of private Lyft ride conversation via unknown number.
- Lyft initially said recording was part of a pilot, later blamed driver.
- Privacy experts say the incident breaches Canada’s federal privacy law.
The woman described feeling stalked and unsafe after receiving a text message which repeated exactly what she had privately discussed with her roommates during their Lyft ride, as first reported by CBC .
Anvi Ahuja had just arrived home from an eight-minute trip on March 11 when she received the unexpected message from an unknown number. “I was like ‘who is taping me?’” she said. “The driver didn’t inform us that we could be recorded,” as reported by CBC.
When she called the number, she heard a standard-sounding Lyft message: “We can’t connect your call because your driver is not available right now.”
Ahuja contacted Lyft immediately. The representative of the company first explained that Lyft was conducting a new feature test. But a week later, Lyft changed its explanation, blaming the driver for recording her without consent and saying “proper actions” were taken, as reported by CBC.
“These ride-sharing apps are big companies and people have a lot of sensitive conversations within cabs and they feel like they’re secure,” Ahuja said, as reported by CBC. “To know that nothing — even beyond our app experience — in the real world is secure anymore is really freaky and uncomfortable to me.”
Lyft confirmed to CBC that it was conducting an in-app audio recording test in certain U.S. cities with strict opt-in rules, but stated that this case was not part of that program.
In a statement reported by CBC, Lyft said: “Safety is fundamental to Lyft… we will investigate and take action for violations.” The company later suggested the transcript might have been generated through a technical mishap involving masked phone numbers.
Privacy experts say this shouldn’t have happened. CBC reports that former Ontario privacy commissioner Ann Cavoukian called it “completely unacceptable,” adding: “Of course, you assume… conversations with people in the car [won’t be] taped and transcribed.”
According to Canadian privacy laws, companies must clearly inform and get consent from passengers before recording. “They would definitely need to obtain passengers’ meaningful consent,” said Anaïs Bussières McNicoll from the Canadian Civil Liberties Association.
“Even if I’m one of the very few people that experienced this,” Ahuja said, “I’m still concerned about what happens to our data and our privacy — which is a responsibility that Lyft has to its customers.”