
Image by Freepik
AI-Created Works Get Copyright Green Light, Says The U.S. Copyright Office
- Written by Kiara Fabbri Former Tech News Writer
- Fact-Checked by Justyn Newman Former Lead Cybersecurity Editor
The U.S. Copyright Office has clarified that artists can copyright works created with the assistance of artificial intelligence, as long as human creativity is evident in the final product.
In a Rush? Here are the Quick Facts!
- Human creativity must be evident for AI-assisted works to qualify for copyright protection.
- Fully machine-generated works are not eligible for copyright protection.
- The Copyright Office plans a separate report on AI training, licensing, and liability.
This decision, outlined in a report released Wednesday, could influence how AI-generated content is treated in industries such as music, film, and publishing.
The office, which operates under the Library of Congress, processes around 500,000 copyright applications annually, increasingly including AI-generated works. While each case is assessed individually, the report affirms that copyright protection hinges on human authorship.
Shira Perlmutter, Register of Copyrights, emphasized that human creativity remains central to copyright eligibility. “Where that creativity is expressed through the use of AI systems, it continues to enjoy protection,” she stated, as reported by the AP .
The report explains that AI-assisted works may qualify for copyright if an artist’s contribution—such as modifying or arranging AI-generated content—demonstrates originality.
However, fully machine-generated works remain ineligible. Simply prompting an AI system to generate content does not grant copyright ownership. The report argues that extending protections to works where the expressive elements are determined by a machine would undermine copyright’s purpose, as reported by the AP.
The report follows a review launched in 2023, which gathered feedback from AI developers, artists, and other stakeholders. It does not address the ongoing controversy over AI companies using copyrighted material without permission to train their models, notes the AP.
Numerous lawsuits from artists , authors, and news organizations accuse AI firms of copyright infringement, a legal battle that remains unresolved.
While the Copyright Office does not rule on these disputes, it is preparing a separate report to examine issues related to AI training on copyrighted works, potential licensing frameworks, and liability concerns.
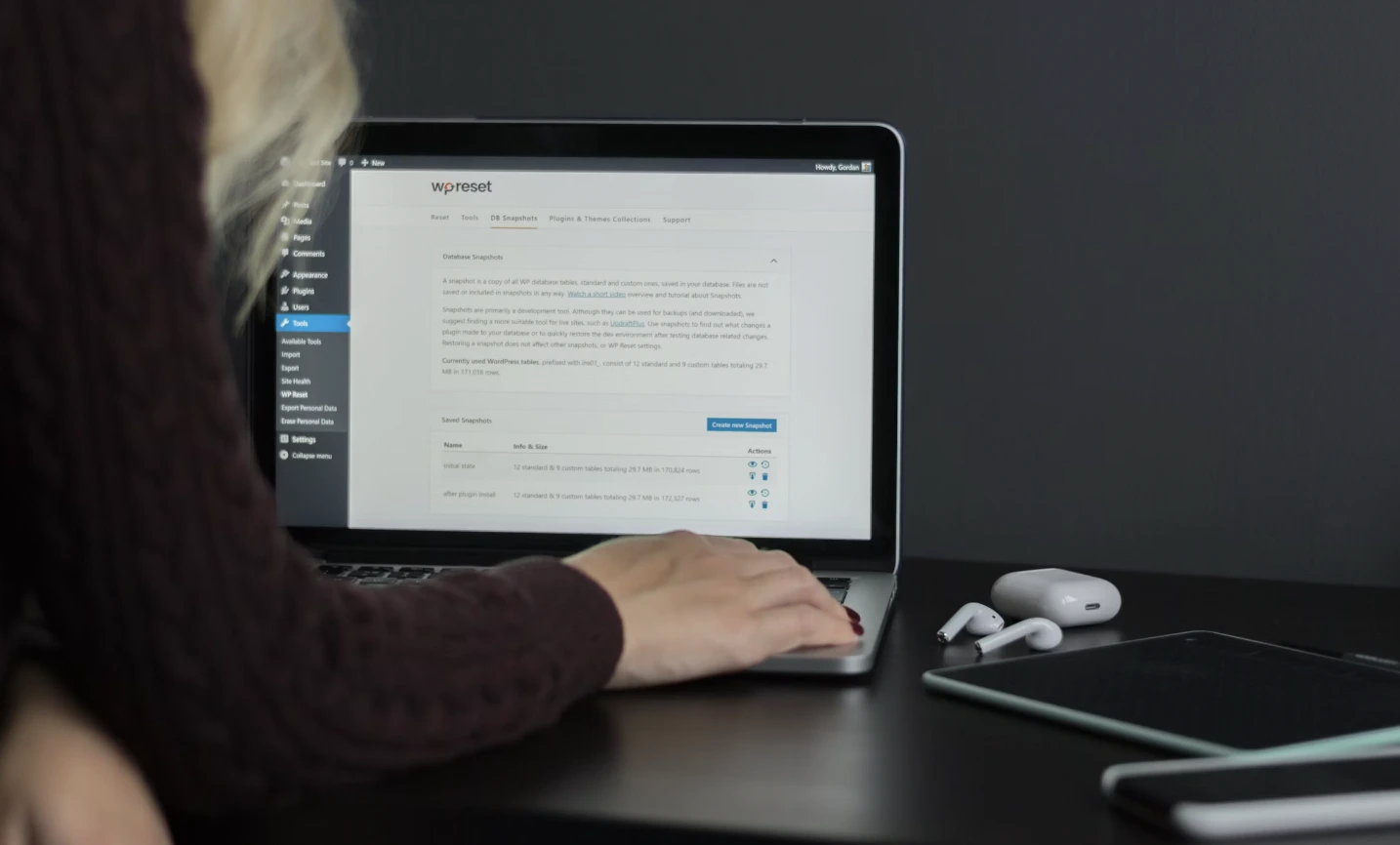
Image by WebFactory Ltd, from Unsplash
10,000 WordPress Sites Hacked To Spread Malware
- Written by Kiara Fabbri Former Tech News Writer
- Fact-Checked by Justyn Newman Former Lead Cybersecurity Editor
Over 10,000 WordPress websites have been hacked to distribute malware targeting both Windows and macOS users, security researchers at c/side revealed this week.
In a Rush? Here are the Quick Facts!
- Attackers target outdated WordPress plugins to inject malicious JavaScript.
- Malware includes AMOS for macOS and SocGholish for Windows.
- Fake Google Chrome update prompts trick users into downloading malware.
Attackers injected malicious JavaScript into outdated WordPress sites, tricking visitors into downloading fake browser updates that install harmful software.
The cybercriminals behind this campaign injected malicious JavaScript into vulnerable WordPress sites. When a visitor lands on an infected page, their browser loads a fake update prompt inside an invisible frame. If a user downloads and installs the supposed update, they unknowingly infect their device with malware.
This method marks a shift from previous tactics, as it is the first known instance of AMOS and SocGholish being delivered through a client-side attack. Instead of redirecting users to a separate malicious site, the malware is injected directly into their browser session.
The AMOS malware is designed to steal sensitive data from Mac users, including passwords, credit card information, and cryptocurrency wallets. It is sold on hacker forums and Telegram channels, making it easily accessible to cybercriminals.
SocGholish, which targets Windows users, is often used to install additional malware, such as ransomware or keyloggers, by disguising itself as a legitimate software update.
The hackers likely gained access to these WordPress sites by exploiting outdated plugins and themes. Since many websites do not have active monitoring for client-side attacks, the malicious scripts went undetected for an extended period.
Security experts identified several suspicious domains involved in the attack, including blackshelter[.]org and blacksaltys[.]com, which redirected users to malware-hosting sites. The malicious script was also found on a widely used content delivery network, making detection more difficult.
To stay safe, website owners are urged to update their WordPress installations and plugins, check for unusual scripts, and remove any suspicious files. Users who may have downloaded files from infected sites should run a full system scan and check their devices for malware.
The campaign highlights the growing threats posed by cybercriminals exploiting website vulnerabilities to infect users with malware. Security researchers are continuing to monitor the attack and warn that more compromised websites may still be spreading the infection.